Setting up a hidden service correctly and securely is sadly still a difficult process. For our third installment of this series I present the following cautionary tale.
Remember hidden services aren't hidden - while the IP addresses of the service is hidden by Tor - the existence of the service is not. If the service doesn't require authentication then anyone with the onion address can access it.
Initially the site looked rather plain, a simple It works! default Apache install. However, the /server-status page told a very different story.
The server was clearly hosted in someones home - as evidenced from a dynamic DNS setup on the observable hostname and that the only clearnet IP accessing the site was it's own.
The server was also hosting two applications - OwnCloud and OpenEnergyMonitor - both being accessed frequently.
OwnCloud (a personal cloud software) servers are not a rare thing on the Dark Web and most are secured appropriately.
OpenEnergyMonitor is "a project to develop open-source energy monitoring tools to help us relate to our use of energy, our energy systems and the challenge of sustainable energy."
I had never heard of it before today, but something about the OpenEnergyMonitor requests stuck out like sore-thumb:
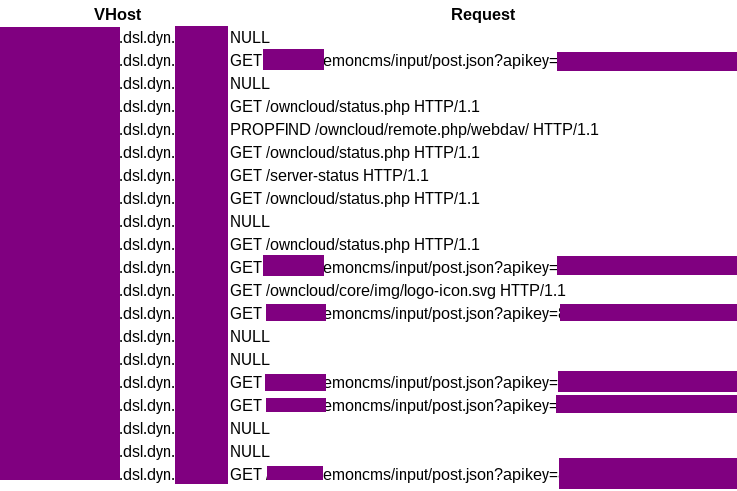
That's right an API key was being passed via the URL! This meant that while the OpenEnergyMonitor instance appeared to have a user name and password, it would be possible to use the API key to nullify that protection!
It should be noted that this is not a fault of OpenEnergyMonitor - it's generally a valid assumption that only authenticated users are permitted to see HTTP request logs - so passing the API key via the URL is likely perfectly safe in most setups that involve OpenEnegyMonitor.
What could be do with that API key if we were so inclined?
- Monitor authenticated feeds, including power usage of any connected devices.
- Publish our own data to screw up monitoring.
- Depending on setup, this kind of monitoring may be tied into other processes; and we could use this to: for example, turn the heating on or off!

But the truth is we don't even need an API key to obtain some information about the monitoring station. OpenEnergyMonitor provides a public API which gives is some data to play with:
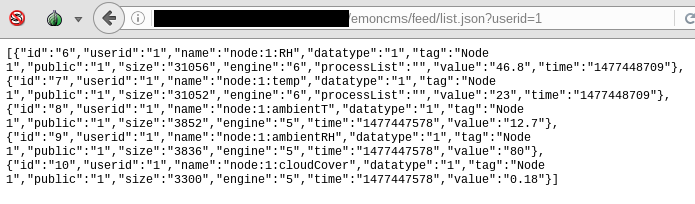
The opsec failures of this server go on - hiding in hidden directories are backups of old Trello boards and other sensitive information. All exposed because of a simple Apache localhost bypass.
There are safe and secure ways to host your IoT setups as a hidden service - this particular case was exposed because of a localhost bypass in Apache, had the hidden service required authentication then even the Apache issue would not have exposed anything.
Note: This is a series of posts chronically some of the more extreme examples of operational security failures discovered by OnionScan
If you would like to support further dark web research and development of tools like OnionScan you can become a patron at Patreon
