Note: This is a new series of posts chronically some of the more extreme examples of operational security failures discovered by OnionScan
For our second cautionary tale, I present the case of Mr. [redacted] a European application developer who has taken it upon himself to sell drugs on the side.
I stumbled upon Mr. [redacted] sites while examining the Apache mod_status leaks discovered during the most recent OnionScan run.
The hidden service site itself is pretty bare, a few drug listings and PGP contact key. It seems this business is a small experiment.

Most server-status exposures are minor in nature, assuming the hidden service is kept on an isolated server - even if that servers identity is leaked it still requires the legal force of a warrant to jumpstart the investigation again.
However, not in the case of Mr. [redacted] - for you see, for what ever reason, he hosts the site for his newly founded application development business on the same server as his drug business.
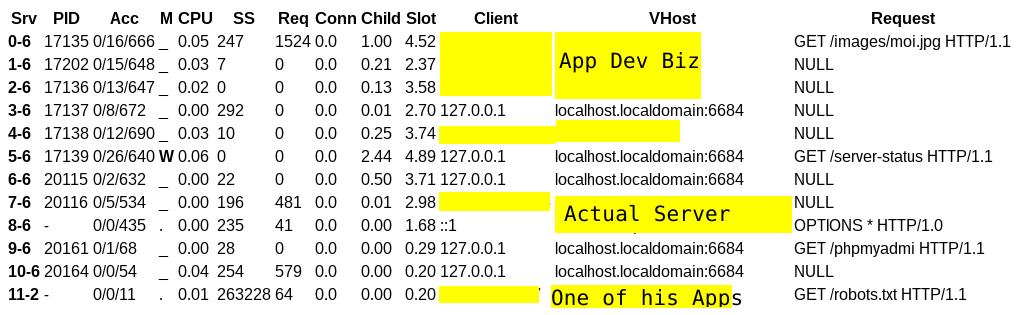
This means the server-status leak not only exposes the location of the server hosting the drug advertisement. It also points directly to the identity of the man behind it all.
I will end this entry here because otherwise it just gets worse.
