When a source wants to leak information, they must first become aware of their options & take steps to protect their operational security.
However the very act of seeking out, researching and accessing this information can place a source at risk of discovery.
Overview: The First Contact Problem
This first contact problem is an artifact of most privacy and anonymity systems - how do you gain access to a system that protects your privacy in a private fashion?.
This article will examine some of the common ways in which the current leaking pipeline...leaks.
Problem: Choosing Where To Leak
Let us imagine that a source has heard of SecureDrop, and that they know that some organizations use it to protect sources.
Perhaps the source is fond of The Guardian and is aware that they have a secure drop instances at: https://securedrop.theguardian.com/ and they visit the page...
In that one act the source has potentially compromised themselves.
Between entering the URL in the bar and the page loading they have twice associated a reference between SecureDrop and themselves (or at least their IP address).
Once in the DNS request for securedrop.theguardian.com and once in the TLS SNI extension:
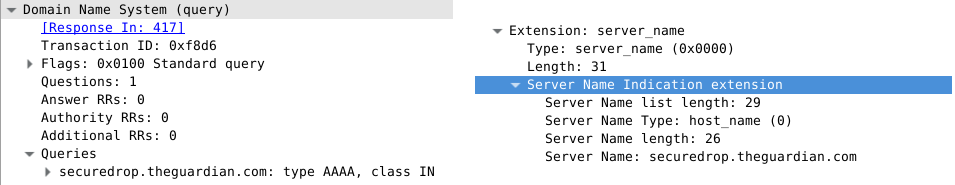
Now it is important to state that neither of these metdata leaks by themselves or even together are substantial evidence of someone leaking - but during an investigation they could act as a smoking gun.
It it worth remembering at this point that multiple governments now require Internet Service Providers to keep a record of sites visited - and that we know other government departments regularly intercept Internet traffic and make such data available during investigations. An investigation having access to such information is no idle fantasy.
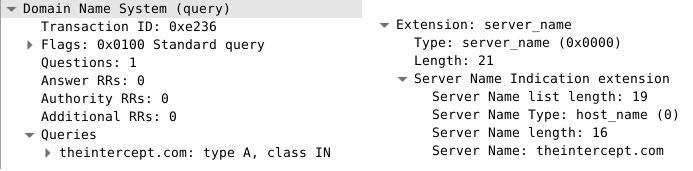
The above discoveries can be mitigated by hosting SecureDrop information as part of the main news site e.g. https://theintercept.com/securedrop/
This ensures that direct references to SecureDrop does not show up in DNS requests or the SNI extension.
Alternatively using Tor or a non-personal Internet connection also reduces the risk of association. However, these solutions also beget problems.
Problem: Acquiring and Using Tor Browser
The same DNS/SNI issues arises when downloading the Tor browser. Most sources are likely going to end up on the Tor Project's website and this fact will be exposed by their network traffic.
A further complication arises once they start using Tor. Tor traffic can be fingerprinted and thus it should be assumed that ISPs and others with access to traffic logs can construct activity logs for when people start and stop using Tor.
For sources who start using Tor immediately prior to leaking sensitive information this is another smoking gun during an investigation and one which we must assume will be used.
Possible Solutions
Providing potential sources immediate access to Tor is essential in ensuring that their activities are not caught up in the drift net of mass surveillance.
Emphasizing the importance of everyone using Tor as part of regular Internet activity is essential. The more people who use Tor, the harder it is for any one person to be singled out.
Having a history of using Tor might single a source out - so it is essential not only that they have a history of using Tor, but that others around them do also.
Outside of a personal environment there are other options - informing potential sources to use non-personal Internet connections e.g. coffee shops is also a good tactic when it comes to disassociating traffic data. However there are also various operational risks associated with public settings.
Providing potential sources immediate access to Tor is essential in ensuring that their activities are not caught up in the drift net of mass surveillance.
In that vein The Library Freedom Project has worked with libraries to make Tor available on community computers - making it easy for anyone to access anonymous resources without compromising clearnet metadata. Such schemes are likely necessary if we wish to protect a wide variety of potential sources.
Document Metadata
Finally, we must talk about the problem of document metadata. Most potential sources are unlikely to have any knowledge regarding the kinds of information that a word document, PDF or image contains.
While SecureDrop contains software allowing journalists to inspect and remove metadata - we must consider the case where sources wish to keep this information hidden.
Practically every Darknet Marketplace now removes EXIF data from uploaded images - inspired by years of vendors making trivial opsec mistakes while uploading.
We need to be build tools that allow sources to inspect what metadata various documents contain and provide them with the ability to scrub them themselves - before interacting with SecureDrop.
This creates yet another first contact problem like the ones above - but like those I believe this one is solvable.
SecureDrop could of course purge all metadata on upload, like darknet markets do - but we must take into account a threat model where a news organization or SecureDrop instance is compromised - and aim to protect the source from such a risk.
A generally marketable privacy extension for documents and images ("see what kind of information you are sharing") could gain enough ground to be known and help sources making these decisions.
Right now, searching for any information on document metadata brings up a variety of technical documents with very little aimed at a general audience.
Moving Forward
New technology and innovations in user experience can make being an anonymous source less risky.
In addition, general education about the privacy concerns of Internet & document metadata are essential in helping sources make choices that protect themselves far before they engage with someone with more expertise in operational security.
In an age where leaking might be the only way to gain access to accurate information regarding the state of various government departments, we should do everything we can to make it as easy, and as safe, as possible.
Sarah is a privacy & anonymity researcher working to make the world a fairer place. If you would like to support her research and development of tools like OnionScan you can become a patron at Patreon
