I recently had an email conversation with a hidden service owner who had mod_status exposed. When reporting the issue the owner initially was sceptical about how bad this kind of attack could be - thankfully after some back-and-forth I was able to explain the severity of the issue, and that hidden service is now mod_status free!
Inspired by the exchange, this article will detail some of the more extreme examples of mod_status failures I have found through the OnionScan project to hopefully serve as a reference for current and future site admins.
Brief Introduction
For those unaware mod_status is an Apache module which presents a single page at /server-status which contains a number of analytics about the server.
The main defence mod_status has from unauthorised eyes is that it is only available from localhost.
If you know anything about hidden service then you may be able to see the issue - all onion services receive traffic as if the traffic is coming from localhost. The availability of mod_status in this context is an example of a localhost bypass attack.
With that under our belts, let's take a look at some real world examples of how bad these kind of leaks can get.
Exposing Client Activity
A few weeks ago I came across a dark web search engine for books - the site had an exposed mod_status endpoint leading to the leaking of site searches, with expected results:
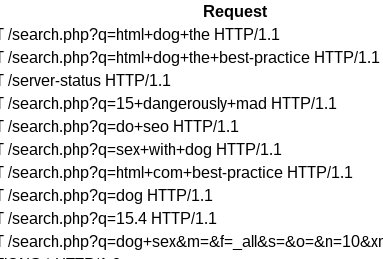
As well has dodgy searches, I have also come across services leaking shopping habits, bitcoin transaction ids, encryption keys (sent via GET request) and various other secret data being shared via URLs.
Exposing Clearnet Clients
In the case of the hidden service mentioned in the introduction, it happened to be co-hosted on the same server serving the clearnet version of the site. This meant that the mod_status leak exposed all the clearnet clients who were connecting to the server, as well as their browsing habits.
Exposing Co-hosted Hidden Services
Perhaps one of the most damning leaks from a server admins point of view is leaking all the different hidden services hosted on the same server instance - as well as their activity.
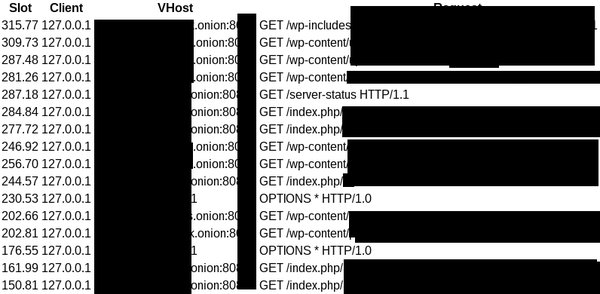
The OnionScan project has been able to use these leaks to produce more detailed connection maps of the dark web.
Exposing Server IP Address
Finally, the killer mod_status leak is simply exposing the servers actual IP address. This is often game over from an anonymity perspective. There are a small number of these leaks around the dark web:
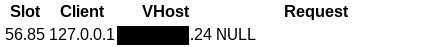
It may already be too late.
I have been on a vendetta of sorts since the beginning of 2016 to try and reduce the number of hidden services exposing mod_status.
Sadly, the needle has not moved much and still, as of the time of writing this article, 6% of hidden services expose some level of information through mod_status.
The data has already been captured and leaked - if you are an affected hidden service owner the best you can do now is damage control.
