tl;dr: Bounce is an experimental authentication system designed to get rid of passwords, databases and a reliance on email for anonymous user systems. Bounce uses Ricochet as a means to offer authenticated, anonymous, pseudonyms! You can try out a demo at: http://trc4t4bl7d65hdiq.onion
I hate passwords, I hate user databases and I hate email,
All of these complicate the threat model for building anonymous pseudonyms and require significant investment to keep people safe.
Passwords are required to be static, complex and unique - so much so they now require an entire new application just to manage all the different passwords needed to access any single account.
And the fun doesn't stop there! Application owners need to be responsible in designing and maintaining databases with appropriate levels of encryption and building password reset flows for account recovery.
Finally, those password reset flows often rely on email. Email requires a mail server which, if you are sensible, is maintained by someone else.
Setting up a secure, anonymous email account is difficult. Depending on your baseline knowledge and access to good recommendations you hopefully luck out with a good host who isn't logging and inspecting all your incoming an outgoing mail mining metadata and content (of course the network is likely doing that anyway!) - and if you are savvy enough to encrypt, well then you just have to hope whoever built the password reset flow also collected your public key...otherwise your anonymous account is easily compromisable by a bad email provider or network actor.
This article outlines a plan for a better way.
Introducing Bounce

Bounce is an experimental authentication prototype. Bounce uses Ricochet as a means to offer authenticated, anonymous, pseudonyms!
This has several advantages over traditional user management solutions:
- Anonymity - Using the power of Ricochet and Tor, the user can disassociate themselves from the account, without having to setup an anonymous email account - which is often fraught with difficulties.
- No Passwords to remember - Authentication is provided through the authentication properties of Tor Hidden Services (through Ricochet). Of course, there is nothing to stop someone extending Bounce to also ask for another authentication factor! Which brings us to...
- Decentralization - Anyone can run a Bounce server, allowing users to pick and choose which entities get to know which of their ricochet addresses. Sites do not have to rely 3rd party providers to allow a consistent user experience across different sites.
How Does Bounce Work?
Bounce is fairly simple.
- The user is asked for a ricochet address, which is passed on to the Bounce Service.
- Bounce then constructs an encrypted token and sends a message to the ricochet address.
- The user receives the token and copies it like a password into a login box on the website.
- Bounce validates the token and, if it is valid, logs the user in - this token can then be set as a cookie that is checked on every interaction.
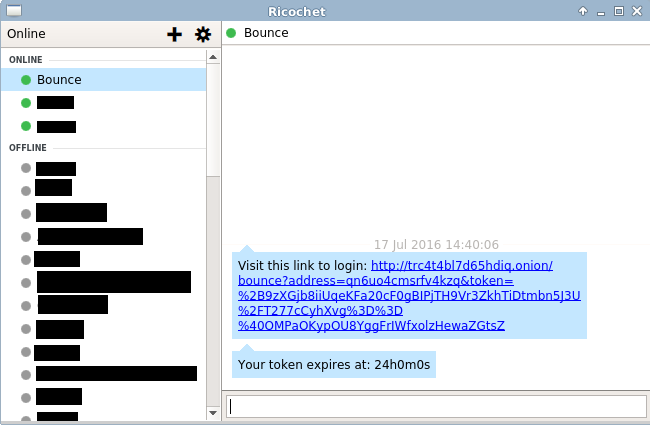
Bounce Tokens are databaseless and stateless - they do not require an infrastructure to store, and can be reused until they expire - the expiration is baked into the token and is verified by the bounce server.
How does this compare to Passwords and 2FA?
I believe that a scheme like Bounce would be superior to the current password based schemes of many websites - especially those that require anonymous accounts.
- An adversary who does not have access to your ricochet private key cannot login to the site - in contrast to passwords which are static and guessable.
- There are no need for complex password requirements.
- Sites do not need to store any sensitive authentication information like e.g. passwords - Sites just need to store any user information, which they can associate with the ricochet id. Nothing to store, means nothing to leak.
- Users can reuse the same ricochet id across multiple sites - no need to remember different passwords or need for a password manager.
The only attack that Bounce cannot defend against is malware residing on the users computer stealing authentication links. It is worth noting that passwords along cannot defend against this attack either.
Two-factor Authentication can be used to minimize the surface of a malware based attack, and indeed, this is the only scenario where 2FA is still needed in an auth scheme using Bounce (contrasting to a password scheme where 2FA is needed to defend against password leaks from other sites)
Can I Use Bounce Right Now?
Kinda. It is very much a prototype, relying on another prototype (go-ricochet). Bounce has not undergone a security audit and, as the creator, I would not recommend you use this for a site that requires anything above low levels of security.
However, the code is open source, and you can demo Bounce by visiting http://trc4t4bl7d65hdiq.onion. The code for this example can be found on github.
